Sage XRT Business Exchange 15 (2023 R1)
File Transfer service
Securing Server Protocols
Logins Management
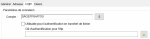
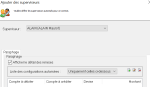
The server protocols exchanges can be authenticated.
For financial operators, select the option: Usable for authentication in file transfer.
You can enter the authentication key to use with SFTP protocol.
When you use the financial operator, login-password management and its complexity are delegated to Sage XRT Common Services.
Server Protocols
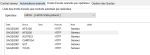
For HTTP, SFTP, FTP and AS2 protocols, access rights to the monitored contracts must be granted to the operator.
The Advanced authorizations enable you to add quickly the list of the monitored contracts.
Quotas Management
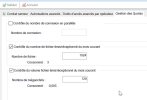
You can define a number of simultaneous connections. The default number for one entity is ten simultaneous connections.
You can also perform monthly checks over the number or the total volume (in MB) of sent and received files. Once the quotas are reached, every new connection is refused.
All the parameters are checked after the login, then both volumetric parameters linked to the files are checked on each creation and retrieval queries to the server.
Management of Maximum Connection Time
To prevent any client connections from remaining active all day long, checks on the KeepAlive and NOOP commands must be performed for SFTP and FTP server protocols.
When a certain number of consecutive KeepAlive commands is reached, the connection is deactivated. This limit is settable. When any other command than KeepAlive is sent, the counter is reset.
When the Authorize KeepAlive commands parameter is set to YES, KeepAlive commands keep the connection active. This is the default behavior for any Sage XRT Business Exchange version before version 15 (2023 R1).
When the Authorize KeepAlive commands parameter is set to NO, KeepAlive commands cannot keep the connection active. This is the default behavior of all versions as of version 15.
Cryptographic Options for SFTP
For the File Transfer Service, the set of securing protocol can be defined:
Proposal KEyExchange Alg: algorithm for key exchanges (the available values are the same as the ones recommended in 2021: diffie-hellman-group-exchange-sha256)
Proposal Encrypt Alg: encryption algorithm
Proposal HMAC alg: HMAC algorithm which calculates the integrity of network frames of SFTP protocol
Proposal Compression Alg: compression algorithm used in the exchanges
You can also define the level of log: four levels of info. are available for traces.
eecdh-sha2-nistp256, ecdh-sha2-nistp384, ecdh-sha2-nistp521, diffie-hellman-group-exchange-sha256
diffie-hellman-group-exchange-sha1, diffie-hellman-group14-sha1, diffie-hellman-group1-sha1
aes128-ctr, aes192-ctr, aes256-ctr
arcfour256, arcfour128, aes128-cbc, 3des-cbc, blowfish-cbc, cast128-cbc, aes192-cbc, aes256-cbc, arcfour, [email protected]
[email protected], [email protected], hmac-sha2-256, hmac-sha2-512
[email protected], [email protected], [email protected], hmac-md5, hmac-sha1, [email protected]
hmac-ripemd160, [email protected], hmac-sha1-96, hmac-md5-96
ecdh-sha2-nistp256, ecdh-sha2-nistp384, ecdh-sha2-nistp521, diffie-hellman-group-exchange-sha256
diffie-hellman-group16-sha512, diffie-hellman-group18-sha512, diffie-hellman-group14-sha256, diffie-hellman-group14-sha1
iffie-hellman-group1-sha1, diffie-hellman-group-exchange-sha1
aes128-ctr, aes192-ctr, aes256-ctr
aes256-cbc, [email protected], aes192-cbc, aes128-cbc, blowfish-cbc, arcfour128, arcfour256, cast128-cbc, 3des-cbc
hmac-sha2-256, hmac-sha2-512
hmac-sha1, hmac-sha1-96, hmac-md5, hmac-md5-96, hmac-ripemd160, [email protected]
These parameters are not defined by default.
File Transfers
Application Redesign
Sage XRT File Transfers Application has been redesigned with Carbon architecture and Rest API to for a smooth operation with the various Sage XRT Online Banking modules.
Authentication
When sending or receiving files, you are authenticated by your connection login.
Sage XRT File Transfers application is not available for the users of SAAS group.
File Types
You can issue a file for one of the set up contracts and make it available.
You can extract all file types available and whose extension is supported by the operating system.
When several files are extracted at the same time, a zipped file is created for each service type.
The default name for the extracted file is the file alias. If no alias is specified, the extracted file uses the name of the original file.
You can click a file number to view the file in a new tab. If the type of the file cannot be displayed, a message asks whether you want to download it.
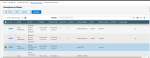
Transfer History
The transfer history allows you to view the results of transmissions and receptions.
Signature
Supporting Documents
Addition
A new Attachments column is available on the Add page of the signature workflow.
For each file, you can add one or more documents by clicking the button in the corresponding Attachments column.
The buttons with the Plus sign and the Bin enable you to add and remove attachments.
Once the documents are added, the Attachments column displays their names.
Signature and Preparation
You can also add documents during the files Preparation and Signature phases
For each file, you can add one or more documents by clicking the button in the corresponding Attachments column. The number of attached documents is also displayed in this column.
Documents can only be deleted during Preparation. The Description column cannot be modified.
Click the document in the Name column to save it or to display it a a new tab.
Comments
A new Comments column is available in the list of files to sign. On each file, you may add comments to start chatting with the other signatories. The number of messages added to this discussion is displayed.
Click the Message button or the number specified to display the chat box.
All the signatories of the file can see a comment as soon as it is entered and validated.
Each signatory can delete their own comments.
If a Description has been specified during the addition, it is used as the chat title.
XaDES Signature
The XaDES format is available as a real signature for the signature station with the required license. It is available under Windows. The minimum version of EidSign is 4.0.0.108.
For large files, the variable Max Xml File length for XADES is available in the registry. This variable is positioned to 150 MB: beyond that limit, the signature is detached, below, the signature is enclosed.
Certificate with Not Initialized Status
In the Setup for EBICS identities, a signatory can force the status of their certificate to Not initialized.
This enables the renewal of the initialization with your banking partner.
Authorized Configuration Options for Contracts
For a smoother setup process of Preparation, Supervisors, Initialing and Bank Delegations for signatories, the list of Authorized Configurations presents two options in the Contract Manager:
Only the following ones
Except the following ones
Supervision
Files and Archives
You can view all the received files and archives.
Simply click the ID number to edit the corresponding file.
The list of the selected files can be exported to Excel.
Interfaces
You can generate your Cash and Reconciliation interface files.
The Generate button enables you to create a file in the directory defined during the setup.
The menu Actions - Download enables you to save the file on your computer.
The menu Actions - Reset Status turns the file status back to Not generated, which enables a new generation.
The menu Actions - Excel enables you to export the list of the selected files to Excel.
Signature Info. in Transaction History
The Additional Information tab is available in the Transaction History for the events for which Transaction = SIGN and Function = SIGN.
Initialing (SIGN), Sending (SEND), Edition (SIGN) of a file and the tickets edition (ARCH) feed both fields:
Number of Transactions: total of the file transactions,
Total Amount: total amount of the file transactions.
File Status
The list of authorized signatories is added into the Signature Workflow tab.
The Additional Information tab is also available.
The Actions menu enables:
the sending of the files at the end of signature workflow, which still await transfer although the signature contract states an automatic transfer,
the unlocking of files.
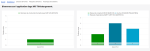
Analysis and Maintenance (P5BAM)
Analysis and Maintenance can be set up by site. The P5bam.ini file must be renamed in the following fashion: P5bam-NomduSite.ini. If there is no file dedicated to a site, the P5bam.ini file is used.
A P5bam.ini file for Oracle is now available. You must delete the P5bam.ini file, and rename the P5bam.ini.oracle file to P5bam.ini.
Two additional sections are available in order to limit analyses and maintenances for the final users.
[USER MODEL LIST], provided with the default analyses: general analysis, analysis of communication contracts, analysis of communication history, analysis of signature service, analysis of today's imports history, extraction of GRPD data, analysis of today's bank accounts.
[USER MAINTENANCE PLAN LIST], provided with the maintenances: contract suspension, reboot of the services with excessive memory consumption (2 GB), temporary file purge, storage of the X509 identities to the safe.
Users from the SAAS group can view analyses and maintenances of the sections [GENERAL MODEL LIST] and [MAINTENANCE PLAN LIST].
Analyses and maintenances can be executed from the Tools menu of Supervision module.
The Edit button enables you to edit the selected analyses.
The following formats are available:
HTML (in a new tab)
TXT
CSV
XML
JSON
In the Actions menu, select Notify to send analyses by email to a group of recipients.
The p5bam.ini file is saved during updates.
EBICS Identities
From the Audit menu, you can view the history of EBICS signatory identities.
From the menu Tools - EBICS Identities, the following actions can be executed for all the EBICS signatory identities:
Restore an EBICS identity that has been wrongly deleted (Deleted status).
Force the status to Not initialized.
General Notifications
General Notifications inform you on all the processing outcome. When available, additional data are displayed.
Accessing Monitored Contracts
The page Access to supervised contracts enables the search for contracts.
New Tabs for Communication
The tabs Description, Protocol Info, Security and Signature Information for sent files are now available.
Platform
Database: VFS Files Size
The size of VFS files is available on TRF_FIC and ARC_FIC tables.
Columns are available in the lists of Supervision module.
After this addition, you may have to update VFS history, including archives.
The Resynchronisation of the file size can be initiated through the PurgeVFS tool.
/ALL Purge of all containers.
/ARCH Purge of the archive container only.
/FILE Purge of the files container only.
/SIGN Purge of the signatures container only.
/S: Purge of one service only.
/DBONLY Purge of Database only.
/DBRESYNC Resync. of file size.
/DSN: ODBC Connection String.
/SERVER: Site Name.
Database: date formats.
To simplify SQL queries, the following columns are added to S_TFI table with the datetime format:
CREDT_TFI, date and time of file
PREDT_TFI, date and time of file addition
PRDT_TFI, date and time of file preparation
The existing column are still fed.
Database: identifiers
To create a link between the files received in Server/Recipient mode for Sage XRT Business Exchange and the files added to signature, two new columns are added:
VFSIDFIC_TFI, file identifier
ARCIDFIC_TFI, archived file identifier
These two columns are added to the Signature pages.
The following arguments are added to PDSCOPY (pdscopy.exe and SXBE objects):
/VFSID, VFS identifier
/ARCID, archive identifier
Rapi Extension for Specific Developments
Rest APIs can be created in P5RAPI service for specific client needs.
Using P5RAPI enables you to inherit from Sage XRT Business Exchange security.
You can access your own data within your various repositories and make new pages developed with Carbon available to clients.
Signature Validation Code
The date of the last modification on the signature validation code is specified in the Change validation code tab.
Usability
In Signature, File Transfers and Supervision modules, you can choose which elements to display.
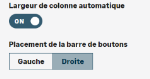
In the User Preferences, you can choose the location of the button bar and activate the auto-sizing of columns.
Usage Statistics of X509/GPG Certificates
The usage statistics enables you to monitor certificates for EBICS, PKCS7 and GPG signature protocols, for maintenance purposes.
Two columns has been added to KEYVAULT table: UCOUNTER and DATE_LAST. They track down the number of usages and the date of planned used certificate.
Red & Purple Teaming (Customer upload)
From Advanced Options in the Data Protection tab, the option Force anti-malware scanning (using antivirus) dynamically activates the Microsoft Antimalware interface.
This option enables the detection of fileless malware attacks. It increases the protection level of received data: surveillance of the JSON files sent on Rapi service coming from EBICS and HTTP protocols en server mode.
The anti-malware analysis also concerns the VBScript and PowerShell scripts, as well as the command lines for processes initiated by Sage XRT Business Exchange.
Improved Tools
Improvements on P5WCERT for GPG:
List of key expiry dates
Keyvault
A new usage of P5WCERT /GPG enables to specifically work on the GPG certificate store. It can be used for /VAL, /EXP, /IMP, /DEL, /DBDEL, /DBEXP, /DBIMP, /CEBCREATE, /CEBREPORT, /CEBDELETE.
PURGEHST enables the deletion of EBICS identities.
Improved Exits
You can make a selection according to the file name through the filter: 12?43*.*.
You can also create a %#tmp1 to %#tmp9 setup to ensure the chaining of the temp files names in exits.
For the protocols supporting Reconciliation, the identifier of the original message is available: #ORIGMSGID. It is also included in the DOM of File Transfer Service under the name: Vfs.OriginalMsgId.
For EBICS protocol, the EBICS order identifier is available: #EBICSORDERID.
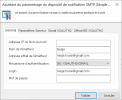
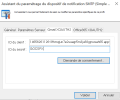
XOAuth2 Support on SMTP Notification Service
XOAuth2 authentication is supported for Gmail and Office 365.
In the General tab of SMTP Notification Device Setup Wizard, select an authentication method: XOAUTH2-GMAIL or XOAUTH2-O365.
Then, in the corresponding tab, specify your identifiers and click Consent Request...
Transparent Modification of ReverseProxy on DMZTools
The proxy service is now based on Windows portproxy interface.
In the Repository tab of Transaction Service, the field OnlineBanking public URL must be specified and the Use transparent proxy option activated.
There is no need to install OnlineBanking and other files on the proxy service.